Category: IT Management
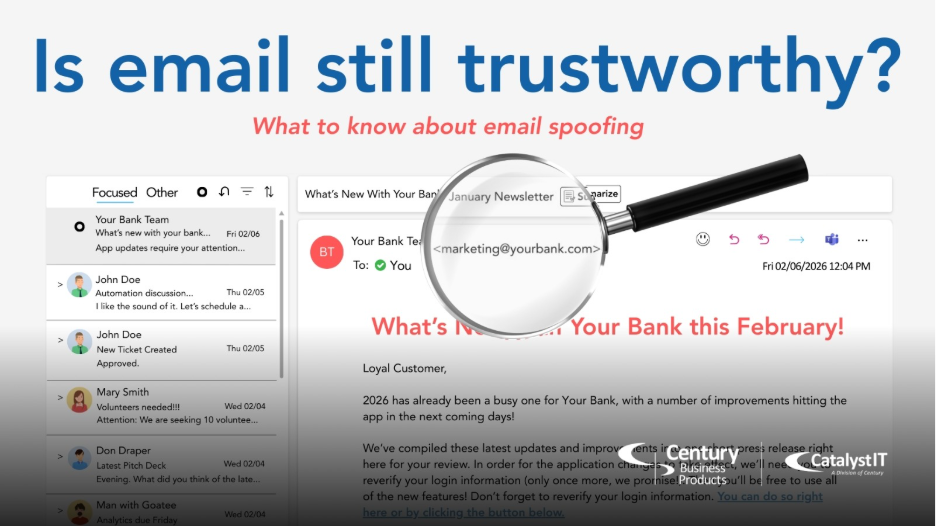
Is Email Still Trustworthy? What to know about Email Spoofing
Your inbox might be lying to you. And cybercriminals are hoping you won’t notice. Most people think email works like Caller ID. If you recognize the phone number, you can trust the caller. That is a dangerous misconception. Imagine receiving an urgent email from your boss and frantically following their instructions… only to find out later that the email didn’t actually come from your boss, even though the “from” address was correct. That’s the very real threat of Email Spoofing. You cannot trust an email simply because you recognize […]

Zero Trust Security: The Mindset Every Business Needs
If a stranger knocked on your door, would you let them walk into your house without verifying who they are? Of course not. Yet that’s exactly how many businesses treat their digital environments by trusting users, devices, and applications without confirming who they are or what they’re doing. Trust is a privilege and a vulnerability. […]

How ‘Free’ AI Tools Put Your Business at Risk
AI-powered tools have become essential in modern workflows, offering automation and convenience. Free AI note-taking apps, in particular, are gaining traction among individuals and businesses looking to simplify documentation. While these free AI tools may seem like a smart shortcut, they often come with hidden risks, especially when it comes to security and compliance. A […]

Copier Technician vs IT Support: Why You Deserve Experts, Not Generalists
In our industry, copier and IT service roles are colliding—they expect IT Support to work on copiers, and copier techs to troubleshoot IT systems. But when specialists are replaced by generalists, is the customer truly getting the support they need? Copier technician and IT support roles vary drastically. Your critical data and technology deserve more than […]

Technology Without Strategy = Expensive Guesswork
Imagine This: Your team is preparing for a major client presentation. The Wi-Fi drops. Your files won’t sync. And no one knows who to call or how to fix it. What starts as a tech hiccup quickly becomes a credibility issue. This kind of disruption isn’t just frustrating—it’s a sign of a deeper problem: missing […]

Anatomy of a Phish: The Psychology Behind Phishing
Much like the Academy Award winning film, Anatomy of a Fall, phishing has everything to do with psychology. Cybersecurity threats aren’t always about complex code or brute-force attacks. Often, the most dangerous breaches start with a simple conversation, a convincing email, or a familiar voice. This is the essence of social engineering—a tactic that manipulates […]

Windows 10 End of Support Guide
It’s fair to say Microsoft has a complicated relationship with Windows 10. Following the less-than-stellar reception of Windows 8, Windows 10 arrived as a beloved successor. Its ease of use and familiarity cemented its popularity. However, that very popularity has created a hurdle, with many users hesitant to embrace the newest operating system (OS), Windows […]

Choosing the Right SaaS Solution for Your Business
Starbucks or Scooter’s? Taco Bell or Taco John’s? Verizon or AT&T? Every day, you’re faced with choices that require decisions. “What do you want for dinner?” may be the most difficult question asked every day. Choosing the right Software-as-a-Service (SaaS) for your business can be just as difficult, probably more so. The allure of SaaS […]
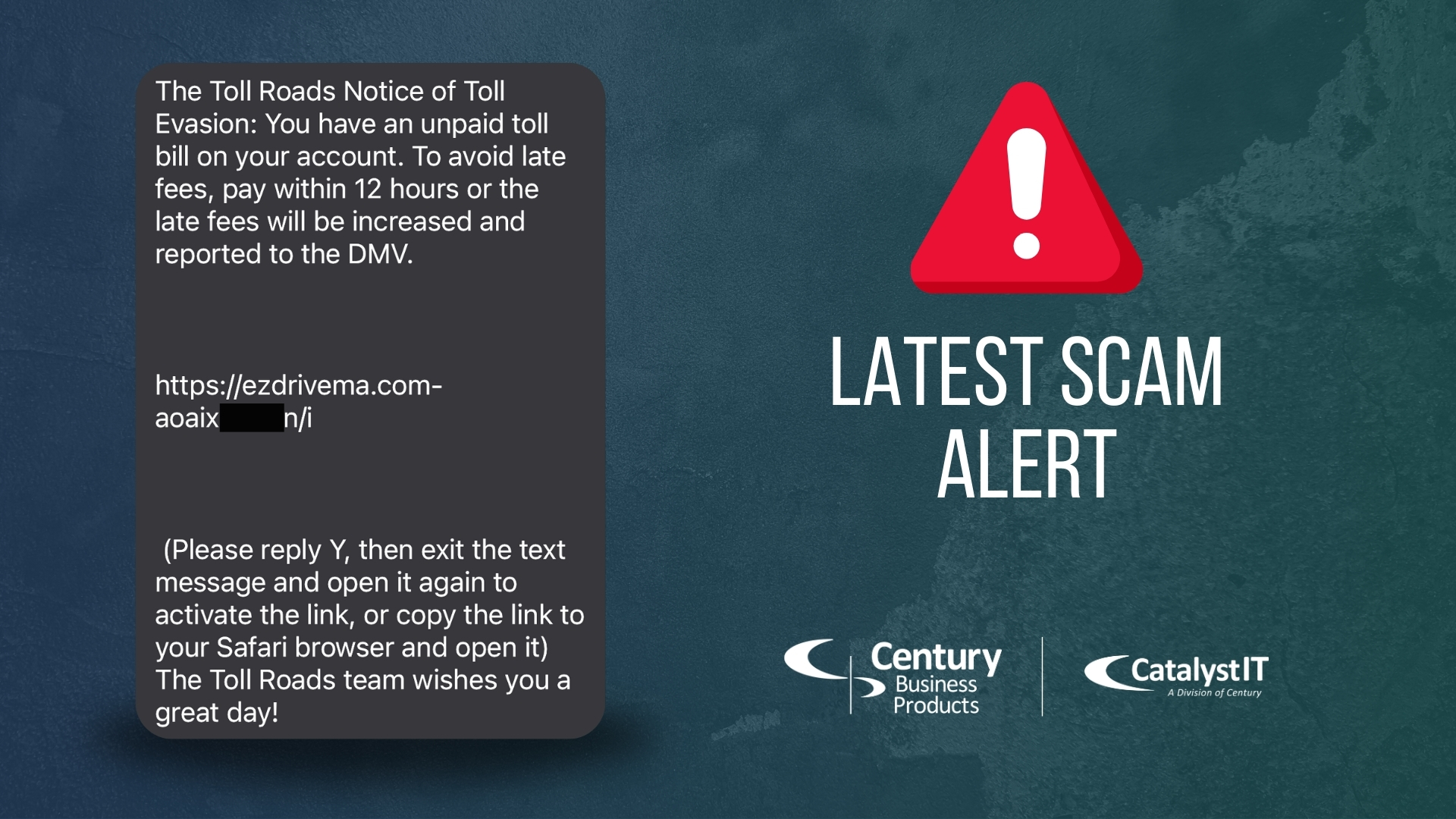
The Latest Text Message Smishing Scam – Toll Evasion
Be aware of the latest nation-wide text messaging scam Have you received a text that looks like either of these? These are fraudulent attempts to lure you into divulging person information or downloading malicious viruses. Smishing This type of texting scam is called Smishing, also known as SMS Phishing. Similar to the Phishing emails that you’ve probably […]

Minimizing Third-Party Risks in a Connected World
From supply chain partners to software providers, relying on third-party vendors is essential. These relationships drive our operations. However, every external connection introduces potential risks. Supply chain attacks are no longer a rare occurrence. Cybercriminals actively target vulnerabilities within these complex networks, putting businesses of all sizes at risk. Data breaches, service disruptions, and reputational damage are […]